An OPSGROUP member reported a new GPS spoofing encounter yesterday in the Ankara FIR, while flying southbound between UDVET and INPOR.
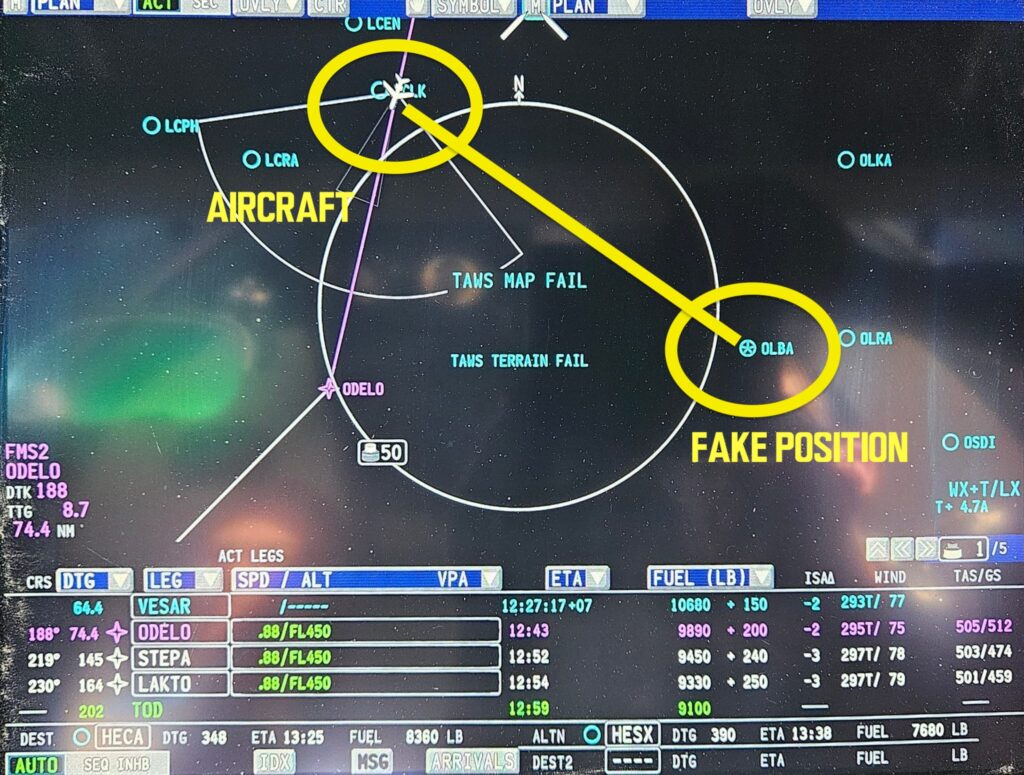
The encounter began around 1200Z, when both selected GPS positions began to show the aircraft position as being over OLBA/Beirut – approx 120nm away.
The crew had disabled GPS inputs prior to the area, but briefly selected them again on the PNF side – when the spoofing began. The route flown during the event was essentially a straight line from LTAF/Adana to LCLK/Larnaca.
The aircraft was a Global Express 7500 at FL470. OLBA/Beirut is in one of the three hotspot areas for GPS spoofing, but this one over Adana is perhaps the furthest away yet to report the problem.
Analysis
This is a great example of how GPS spoofing works. The Nav Display shows the fake GPS position with the star symbol – located exactly at OLBA/Beirut airport.
The aircraft position however – thanks to the crew disabling GPS sensors – is correctly shown over LCLK/Larnaca.
If the crew had not proactively disabled those sensors, the aircraft position would also be shown as over OLBA – and if the spoofing was subtle, the FMS would tend to start suggesting a right turn back to the track inbound ODELO.
Further reading:
- GPS Spoofing Hotspots
- GPS Spoofing QRH – Pilot Guide
- Nov 8 update – Maps, Scenarios, Guidance
- Special Briefings on GPS Spoofing (with reports)
More on the topic:
- More: GPS Spoofing: Final Report published by WorkGroup
- More: Crew Guidance published by GPS Spoofing Workgroup
- More: 400% increase in GPS Spoofing; Workgroup established
- More: NAT Crossing after GPS spoofing: a guide
- More: Outsmarting the GPS spoofers: A clever app
More reading:
- Latest: FAA Warns on Runway Length Data and Overrun Risk
- Latest: EASA’s New Cyber and Data Risk Rule for Operators in Europe
- Latest: Airport Spy: Real World Reports from Crews
- Safe Airspace: Risk Database
- Weekly Ops Bulletin: Subscribe
- Membership plans: Why join OPSGROUP?










 Get the famous weekly
Get the famous weekly 






Spoofing 02 April enroute EGSS to Tbilisi
UM 859 Udros eastbound to destination.
FMS/GPS 1+2 monitor and ADS OUT FAIL
FALCON 7X Fl410
Subsequent sector Tbilisi to Yerevan also failed resulting in a ‘raw data’ VOR approach due ILS INOP.