Key Points
- FAA Enhances Aircraft Privacy: The FAA now allows private aircraft owners to request the removal of personal details from public FAA websites, enhancing privacy.
- US Address Required Abroad: FAA certificate holders abroad must nominate a physical US address by April 2 (for new applicants) or July 7 (for existing holders) to retain their privileges, with professional services available for those without a US address.
- REAL ID Deadline Looms: From May 7, all adult passengers on US commercial flights (including Part 135 charters) must present a REAL ID-compliant ID or other accepted identification, with private Part 91 flights exempt.
- Notam System Fails Again: The US Notam system suffered another outage on March 22, raising concerns about its reliability.
- FAA Tightens KDCA Helicopter Rules: After the Jan 29 mid-air collision, the FAA has closed a KDCA helicopter route, restricted non-essential ops, mandated ADS-B Out, and launched a broader safety review.
- KDCA Drone Tests Trigger Alerts: On March 1, military counter-drone testing near KDCA triggered erroneous TCAS alerts, raising concerns over improper testing and its impact on civil aviation.
In Cognito
On March 28, the FAA began accepting requests from private aircraft owners to withhold personal details (such as name and address) from public access across all FAA websites.
It’s good news for business aviation, as it potentially makes it more difficult for members of the public to track the movement of privately owned aircraft for nefarious purposes.
Aircraft owners can now submit their request via the Civil Aviation Registry (CARES) here.
Address for Service
Attention all FAA License holders abroad – this one’s for you!
The FAA has written a new rule that will require certificate holders abroad to nominate a physical US address for service. We’ve written about it in detail here, but there are essentially two looming deadlines to be aware of:
April 2 for new applications, and July 7 for anyone who already holds FAA certificates, ratings or authorizations. You’ll need to submit this via the USAS website that is about to go live.
Whatever you do – don’t ignore this. If you don’t nominate a US based address by the applicable date, you won’t be able to exercise the privileges of your document. i.e. say sayonara to your license until you submit the right info.
If you don’t have an address to nominate in the US, don’t despair. You can use a professional service like FAA Mail Agent. These guys can take care of all it for less than 50 bucks a year. Use the code ‘Opsgroup’ and get a discount.
Passenger ID Requirements
From May 7, all adult passengers (18+) using commercial air transport within the US (including Part 135 charters) must show an ID that complies with the new Real ID Act.
The big change is that anyone who wants to use a state-issued ID or drivers licence to meet this requirement must make sure that it is REAL ID compliant – look for one of the following symbols:

There is also a list of other IDs (such as US and Foreign Passports) that continue to be acceptable.
Operators need to take note because if they allow a passenger to board an aircraft without the appropriate ID they are effectively breaching TSA requirements and become liable for hefty penalties
Important note – private flights operated under Part 91 are exempt.
The Notam system went kaput (again).
The US Notam system was down (again) for several hours on March 22 due to a hardware failure. It was the second time since early February.

The cause of the latest outage was a hardware failure.
Once again we collectively flinched – a system crash in January 2023 lead to the first US ground stop since 2001, disrupting over 10,000 flights.
Questions are being asked about the reliability of the system, and its lack of redundancy.
The FAA previously announced plans to discontinue the legacy US Notam system by mid-2025, with further changes slated for the next five years.
There appears now renewed public and political concern for a faster resolution.
Mixed Traffic and The Potomac Tragedy
The FAA has responded to several recommendations made by the NTSB in its preliminary report from the mid-air collision over the Potomac River on January 29.
The immediate changes will be felt at KDCA/Washington itself. The FAA has permanently closed the low level helicopter route involved in the accident. Non-essential helicopter ops will also be banned, with increased ATC separation applied to those on ‘urgent missions.’
ADS-B out is now mandated for all helicopters, with only very limited exemptions for presidential missions.
Further afield, the FAA is also looking closely into ops at airports in other major cities with high volumes of mixed traffic (including NY, Boston, Chicago, Dallas, Houston and LA) with corrective actions looming for any risks identified.
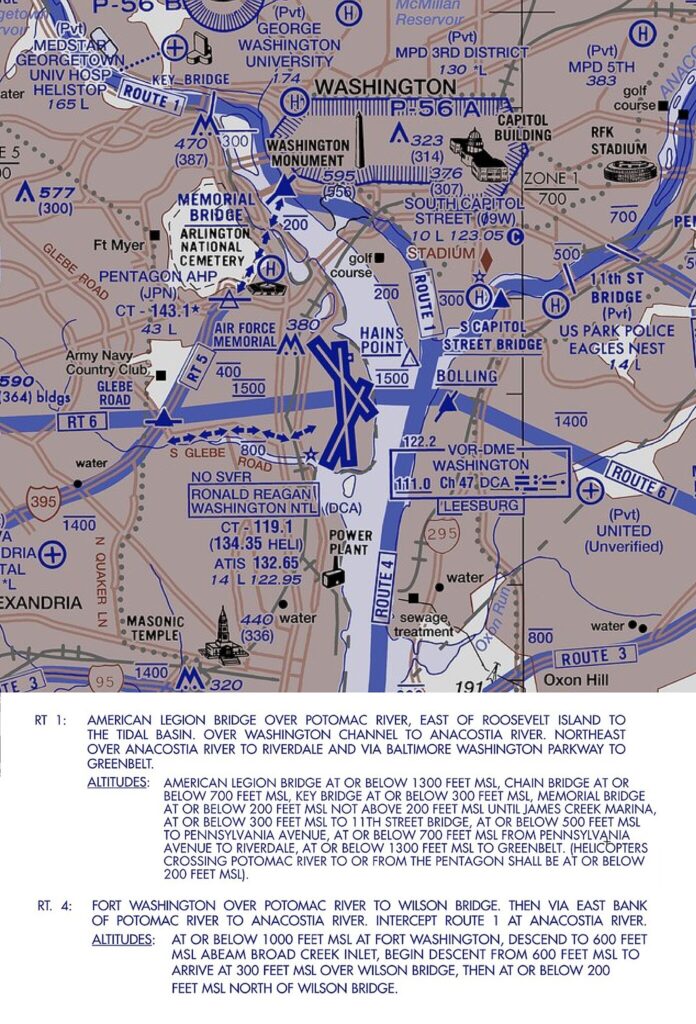
The FAA has announced it will permanently shutter the low level helicopter Route 4.
TCAS wasn’t spoofed in Washington.
On March 1, several aircraft on approach to KDCA/Washington responded to erroneous TCAS alerts, including RAs. While recent research has indicated malicious interference of TCAS is a credible security concern, a Senate hearing last week revealed this was not the case.
The culprit was counter-drone testing by the military nearby which was operating on a similar spectrum to TCAS – a separate concern previously raised by the FAA.
Nevertheless, there are concerns that these tests were conducted improperly and caused unnecessary alarm to civil aircraft nearby. At the very least it was an unfortunate coincidence given recent events at the airport.
Other things you might have missed.
- TFR Busts – The FAA has reported several instances of civil aircraft busting TFRs in recent weeks. The hot spot appears to be Palm Beach, FL where the President has a residence at Mar-a-Lago nearby. A reminder that special procedures apply, including TSA Gateway screening when active for anyone headed in or out of KPBI/Palm Beach. More on that in our recent article, here.
- Laser Strikes – New guidance was published by the FAA on March 26. Turns out the number of laser strikes on aircraft continue to be dangerously high. There’s an online tool to see where the worst spots are here. Remember to report em!
- Drones – DJI, the main recreational drone producer in the US, has removed its built-in geo-fencing feature that physically protects airports from incursions. Instead, an FAA database will simply warn the user when close to a no-fly zone. The issue is that this can now be maliciously ignored. DJI has said that its geo-fencing is about education, not enforcement. We’re not convinced – continue to report any illegal sightings to the FAA.
Anything we missed?
Let us know via news@ops.group, and we’ll add it to this article. As always the team is also available to help answer any questions, or put you in touch with the person who can.

